-
Type:
Incident report
-
Resolution: Fixed
-
Priority:
Minor
-
Affects Version/s: None
-
Component/s: Frontend (F)
-
None
-
Environment:All
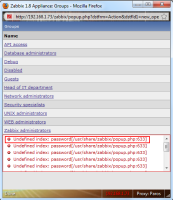
By changing the request parameter to something invalid an error message is produced disclosing the location/path of the zabbix install.
This is an information leakage / path disclosure vulnerability....not a huge deal but should be fixed time permitting.
- is duplicated by
-
ZBX-4668 Path disclosure vulnerability when use API
-
- Closed
-