|
To clarify, I dont care if it is from the onelogin toolkit or implemented another way. I'm just looking for integratable SSO and/or 2FA with Zabbix.
|
|
Related form thread https://www.zabbix.com/forum/showthread.php?t=41432
|
|
I added support for SAML using the Onelogin library and forked the zabbix repo on Github with the changes. You can find the repo at https://github.com/derricksmith/zabbix/tree/Development/frontends/php. You will need to add the following columns to the config table in mysql and add create an sp certificate and key called sp.key/sp.crt located in include/classes/saml/certs/. Still working on single signout.
ALTER TABLE `config` ADD COLUMN `saml_idp_entity_id` text NOT NULL AFTER `ldap_search_attribute`;
ALTER TABLE `config` ADD COLUMN `saml_idp_single_sign_on_service` text NOT NULL AFTER `saml_idp_entity_id`;
ALTER TABLE `config` ADD COLUMN `saml_idp_single_logout_service` text NOT NULL AFTER `saml_idp_single_sign_on_service`;
ALTER TABLE `config` ADD COLUMN `saml_idp_certificate` text NOT NULL AFTER `saml_idp_single_logout_service`;
|
|
I've also started a SAML integration but my question is more around introducing external dependencies.
I don't see any current dependencies in the frontend so are they not allowed? I wouldn't want to re-write a zabbix only implementation of Signed XML just for this feature.
Otherwise I'll have to maintain a fork with SAML similar to @Derrick Smith
|
|
This feature request would provide "Just-in-time" provisioning to allow for users and user group membership to dynamically be applied to Zabbix based upon SAML session values.
I do believe this a feature that is lacking from Zabbix and present in other monitoring solutions. This is a common deliverable in most modern applications and I am hopeful that Zabbix can deliver to compete, if not excel, over other monitoring solutions.
|
|
So I've worked around this in the meantime using mod_auth_mellon (https://github.com/UNINETT/mod_auth_mellon/ - packages in ubuntu repos) in apache2 to integrate with Azure AD and there are a few caveats:
- I still have to manage the account/group permissions in zabbix gui
- this is not a big dealbreaker for us at this stage - it would be nice if group membership data could be fed to zabbix
- you use the enable HTTP authentication options and i recommend ignoring case in usernames
- non "SAML" accounts have to use a separate VHOST to use the zabbix user database or for public "guest" access
- not a deal breaker as we already do this to workaround the lack of user/group level timezone definititions
- no logout from zabbix
Having SAML integrated into Zabbix as a first class citizen would be far far better so that workarounds and kludges don't need to happen for guests or "external" users in particular and as Tim said, Just In Time provisioning and permissions management
i would wholly concur about putting this on the roadmap for a future release
|
|
Hmm zabbix structure is quite particular I assume, since they use no external dependencies and have a bespoke mvc framework. I’ve forked the front end for now to incorporate saml.
|
|
We also have the requirement to change authenticaion to 2FA. Therefor I'd really appreciate this feature to be implemented.
|
|
SAML will be dead at this pace. So, if not SAML with Just in Time Provisioning, then let's root for OpenID Connect with JiT. A case insensitive login via SSO is needed for Zabbix to flourish. Imagine Zabbix Maps that could be freely shared amongst organizations without a drawn out process to create identities in a large organization. Could start encroaching into Atlassian StatusPage business.
|
|
Hello everyone,
Is there is any update on this?
we are using Apereo CAS as an SSO, connecting ZABBIX with it would add many features like Recaptcha v3 and 2FA. In addition, it would provide our IT staff with a seamless experience.
|
|
Resolved in development branch feature/ZBXNEXT-2663-4.5
|
|
Available in:
|
|
Awesome just saw the changelog
|
|
User documentation updated:
|
|
So what is Zabbix's metadata url? index_sso.php?metadata does not work or exist, trying tom import into ADFS or Shibboleth, both require a metadata url for the service provider
|
|
Hello, [email protected]! Zabbix not support metadata.
|
|
So how do you use ADFS without entering any metadata? You cant add the relying party without metadata so you cant use ADFS, but it is shown on the Zabbix Native Integrations page for SAML.
|
|
For others that come across this, I got it working, created a metadata file from scratch for use in ADFS and Shibboleth. Further, I edited sites-available, and added an alias to the metadata file,
*edit - Added a prettier metadata file 
000-default.conf and default-ssl.conf
Alias "/zabbix-metadata.xml" "/var/www/html/zabbix-metadata.xml"
zabbix-metadata.xml
<?xml version="1.0" encoding="utf-8"?>
<EntityDescriptor entityID="https: xmlns="urn:oasis:names:tc:SAML:2.0:metadata">
<SPSSODescriptor protocolSupportEnumeration="urn:oasis:names:tc:SAML:2.0:protocol">
<AssertionConsumerService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST" Location="https: index="0" />
<SingleLogoutService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-Redirect" Location="https: />
<NameIDFormat>urn:oasis:names:tc:SAML:2.0:nameid-format:unspecified</NameIDFormat>
</SPSSODescriptor>
<ContactPerson contactType="administrative">
<GivenName>System Administrator</GivenName>
<EmailAddress>[email protected]</EmailAddress>
</ContactPerson>
<ContactPerson contactType="support">
<GivenName>Tech Support</GivenName>
<EmailAddress>[email protected]</EmailAddress>
</ContactPerson>
</EntityDescriptor>
|
|
we are using this. Works great. Just wanted to let you know and say thanks!
|
|
On this page:
https://support.atlassian.com/security-and-access-policies/docs/configure-saml-single-sign-on-with-an-identity-provider/
are links to examples for different providers.
It might be useful as a reference how to configure it in zabbix.
For Azure AD once we needed to use
as a value for "Username attribute" field.
Yes, it's not a link, but a value for the field. Working example:
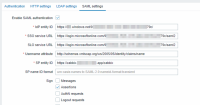
|
Generated at Wed Aug 06 08:54:24 EEST 2025 using Jira 9.12.4#9120004-sha1:625303b708afdb767e17cb2838290c41888e9ff0.
