-
Type:
Defect (Security)
-
Resolution: Fixed
-
Priority:
Blocker
-
Affects Version/s: 4.0.0alpha1
-
Component/s: Frontend (F)
-
Sprint 15, Sprint 16
-
1
There are multiple reflected xss vulnerabilities in frontend.
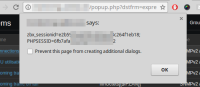
POC is the following maliciously crafted link ("zabbix.internal" should be replaced with your domain name):
http://zabbix.internal/popup.php?dstfrm=expression&dstfld1=itemid&srctbl=items&srcfld2=name&srcfld1=itemid&dstfld2=%22:alert(document.cookie)%2B%22%22,%22
This link leads to a page with item list. Each item name contains onclick handler with injected script.
Clicking on any of the item names causes script execution:
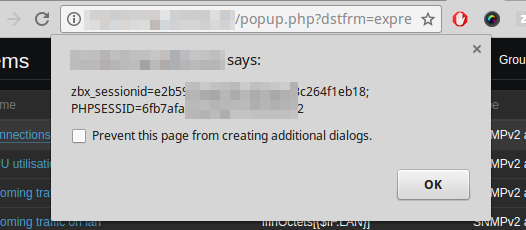
Another example would be the following link:
http://zabbix.internal/screen.import.php?backurl=javascript:alert(document.cookie)&
Click on "Cancel" button will cause execution of injected script.
- depends on
-
ZBX-12768 WASA Findings from NSOC Team
-
- Closed
-