-
Type:
Problem report
-
Resolution: Fixed
-
Priority:
Critical
-
Affects Version/s: 2.2.20, 2.2.21, 3.0.15, 3.4.7
-
Component/s: Agent (G)
-
None
-
Environment:All
-
Sprint 31, Sprint 32
-
0.5
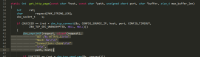
The problem happen in the item "web.page.get[]", which used to "get content of the http web page".
The function handles this item is "get_http_page()" in /libs/zbxsysinfo/common/http.c.
When building the request for http connection, no secure check was made for the parameter in line 41: (see image below).
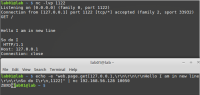
Attacker can add CRLF character to the "path" parameter and freely control the request! (see image below![]()
It can be abused, and used to make tcp request to any local port of the server using zabbix agentd.
For example: Some server using redis, memcached, ... attacker can connect to this port and control it to write file, code execution ...
I don't know this is intent or not but I think it should not be there!
- causes
-
ZBX-15971 Items using: "web.page.*" switch to unsupported when checked service is unavailable
-
- Closed
-