-
Type:
Patch request
-
Resolution: Incomplete
-
Priority:
Trivial
-
None
-
Affects Version/s: 6.0.5
-
Component/s: Proxy (P), Server (S)
-
Environment:Ubuntu 20.04
Zabbix servers with native HA (6.0.5)
Zabbix agents with PSK encryption only (6.0.5)
Steps to reproduce:
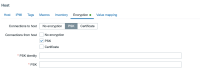
- Deploy agent2 with PSK encryption
- Register host in in zabbix server successfully. Ensure 'Availability' and 'Agent Encryption' are reported as healthy (green) for the host.
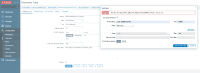
- Go to template, click on discovery rule, click on test
- Fill host address and port and click test button
Result:
We got error:
Get value from agent failed: ZBX_TCP_READ() failed: [104] Connection reset by peer
See screenshot attached (discovery_rule_test.png)
See log file...
In zabbix_agent2.log we got:
cannot process incoming connection: cannot accept unencrypted connection
In zabbix_server.log we don't got any message with standard DebugLevel (3).
In zabbix_server.log with DebugLevel=4 we got:
3491:20220607:142703.312 trapper got '{"request":"item.test","data":{"type":"0","proxy_hostid":"0","key":"vfs.fs.discovery","interface":{"address":"e2.p1.zabbix.opsrv.lan","port":"10050","type":0}},"sid":"7a554f17b555e1a6a2463e9d87bbcf8c"}' 3491:20220607:142703.312 In zbx_trapper_item_test() 3491:20220607:142703.312 In zbx_get_user_from_json() 3491:20220607:142703.312 In DBget_user_by_active_session() sessionid:7a554f17b555e1a6a2463e9d87bbcf8c 3491:20220607:142703.312 query [txnlev:0] [select u.userid,u.roleid,u.username,r.type from sessions s,users u,role r where s.userid=u.userid and s.sessionid='7a554f17b555e1a6a2463e9d87bbcf8c' and s.status=0 and u.roleid=r.roleid] 3491:20220607:142703.312 End of DBget_user_by_active_session():SUCCEED 3491:20220607:142703.312 Permission granted 3491:20220607:142703.312 End of zbx_get_user_from_json():SUCCEED 3491:20220607:142703.313 In zbx_trapper_item_test_run() 3491:20220607:142703.313 In get_value() key:'vfs.fs.discovery' 3491:20220607:142703.313 In get_value_agent() host:'' addr:'e2.p1.zabbix.opsrv.lan' key:'vfs.fs.discovery' conn:'unencrypted' 3491:20220607:142703.313 In is_ip4() ip:'e2.p1.zabbix.opsrv.lan' 3491:20220607:142703.313 End of is_ip4():FAIL 3491:20220607:142703.313 In is_ip6() ip:'e2.p1.zabbix.opsrv.lan' 3491:20220607:142703.313 End of is_ip6():FAIL 3491:20220607:142703.313 Sending [vfs.fs.discovery] 3491:20220607:142703.313 End of get_value_agent():NETWORK_ERROR 3491:20220607:142703.313 Item [:vfs.fs.discovery] error: Get value from agent failed: ZBX_TCP_READ() failed: [104] Connection reset by peer 3491:20220607:142703.313 End of get_value():NETWORK_ERROR 3491:20220607:142703.313 End of zbx_trapper_item_test_run():FAIL 3491:20220607:142703.313 zbx_trapper_item_test() json.buffer:'{"response":"success","data":{"error":"Get value from agent failed: ZBX_TCP_READ() failed: [104] Connection reset by peer"}}' 3491:20220607:142703.313 End of zbx_trapper_item_test()
Why get_value_agent() function is sending request within an unencrypted connection?
Expected:
If we run zabbix_get equivalent command we get correct data:
# zabbix_get -s e2.p1.zabbix.opsrv.lan --tls-connect psk --tls-psk-identity e2.p1.zabbix.opsrv.lan_XXXX --tls-psk-file /path/to_host/psk_secre_file/tls_psk_auto.secret -k vfs.fs.discovery
[{"{#FSNAME}":"/sys","{#FSTYPE}":"sysfs"},{"{#FSNAME}":"/proc","{#FSTYPE}":"proc"},{"{#FSNAME}":"/dev","{#FSTYPE}":"devtmpfs"},{"{#FSNAME}":"/dev/pts","{#FSTYPE}":"devpts"},{"{#FSNAME}":"/run","{#FSTYPE}":"tmpfs"},{"{#FSNAME}":"/","{#FSTYPE}":"xfs"},{"{#FSNAME}":"/sys/kernel/security","{#FSTYPE}":"securityfs"},{"{#FSNAME}":"/dev/shm","{#FSTYPE}":"tmpfs"},{"{#FSNAME}":"/run/lock","{#FSTYPE}":"tmpfs"},{"{#FSNAME}":"/sys/fs/cgroup","{#FSTYPE}":"tmpfs"},{"{#FSNAME}":"/sys/fs/cgroup/unified","{#FSTYPE}":"cgroup2"},{"{#FSNAME}":"/sys/fs/cgroup/systemd","{#FSTYPE}":"cgroup"},{"{#FSNAME}":"/sys/fs/pstore","{#FSTYPE}":"pstore"},{"{#FSNAME}":"/sys/fs/bpf","{#FSTYPE}":"bpf"},{"{#FSNAME}":"/sys/fs/cgroup/rdma","{#FSTYPE}":"cgroup"},{"{#FSNAME}":"/sys/fs/cgroup/freezer","{#FSTYPE}":"cgroup"},{"{#FSNAME}":"/sys/fs/cgroup/pids","{#FSTYPE}":"cgroup"},{"{#FSNAME}":"/sys/fs/cgroup/blkio","{#FSTYPE}":"cgroup"},{"{#FSNAME}":"/sys/fs/cgroup/net_cls,net_prio","{#FSTYPE}":"cgroup"},{"{#FSNAME}":"/sys/fs/cgroup/cpuset","{#FSTYPE}":"cgroup"},{"{#FSNAME}":"/sys/fs/cgroup/hugetlb","{#FSTYPE}":"cgroup"},{"{#FSNAME}":"/sys/fs/cgroup/devices","{#FSTYPE}":"cgroup"},{"{#FSNAME}":"/sys/fs/cgroup/perf_event","{#FSTYPE}":"cgroup"},{"{#FSNAME}":"/sys/fs/cgroup/cpu,cpuacct","{#FSTYPE}":"cgroup"},{"{#FSNAME}":"/sys/fs/cgroup/memory","{#FSTYPE}":"cgroup"},{"{#FSNAME}":"/proc/sys/fs/binfmt_misc","{#FSTYPE}":"autofs"},{"{#FSNAME}":"/dev/hugepages","{#FSTYPE}":"hugetlbfs"},{"{#FSNAME}":"/dev/mqueue","{#FSTYPE}":"mqueue"},{"{#FSNAME}":"/sys/kernel/debug","{#FSTYPE}":"debugfs"},{"{#FSNAME}":"/sys/kernel/tracing","{#FSTYPE}":"tracefs"},{"{#FSNAME}":"/sys/fs/fuse/connections","{#FSTYPE}":"fusectl"},{"{#FSNAME}":"/sys/kernel/config","{#FSTYPE}":"configfs"},{"{#FSNAME}":"/boot","{#FSTYPE}":"ext4"},{"{#FSNAME}":"/opt","{#FSTYPE}":"xfs"},{"{#FSNAME}":"/run/user/0","{#FSTYPE}":"tmpfs"}]
#