-
Type:
Sub-task
-
Resolution: Fixed
-
Priority:
Major
-
Affects Version/s: 6.0.20, 6.4.5, 7.0.0alpha3
-
Component/s: Agent2 plugin (G)
-
Sprint 103 (Aug 2023)
-
4
During the work on the parent issue the incorrect behaviour of TLSConnect parameters with verify_ca and verify_full values was noticed in the PostgreSQL plugin. It differs from the parameters providing the same functionality that are used by the psql command line client. Current behaviour doesn't allow you to check the server certificate without having to provide client certificate and key.
For example:
1. Set up server-side encryption with the server certificate signed by CA according to the PostgreSQL documentation (https://www.postgresql.org/docs/current/ssl-tcp.html). Or you could create self-signed certificate and also use it as the CA certificate in the following steps.
2. Set up monitoring according to the template documentation (see the updated README.md of "PostgreSQL by Zabbix agent 2" template in the parent task). Usage of TLS will require the addition of named session, so you could add the following parameters in the existing configuration file or create a new one (session name is myconn):
# Set up connection URI, replace <instanceip> with the IP or hostname of the monitored instance Plugins.PostgreSQL.Sessions.myconn.Uri=tcp://<instanceip>:5432 # Set up encryption mode to "verify_ca" (or "verify_full" if you also want to check the host name) Plugins.PostgreSQL.Sessions.myconn.TLSConnect=verify_ca #Plugins.PostgreSQL.Sessions.myconn.TLSConnect=verify_full # Set up the path to the CA certificate which was used to sign the server certificate (copy it to the host on which Zabbix agent is installed beforehand): Plugins.PostgreSQL.Sessions.myconn.TLSCAFile=/var/lib/zabbix/.postgresql/root.crt
3. Specify the session name in the {$PG.CONNSTRING} macro and password in {$PG.PASSWORD} macro.
4. Test any Zabbix agent item, for example "PostgreSQL: Get connections sum".
Result:
An error will be shown, saying that we did not specify the client certificate (and hence client key).
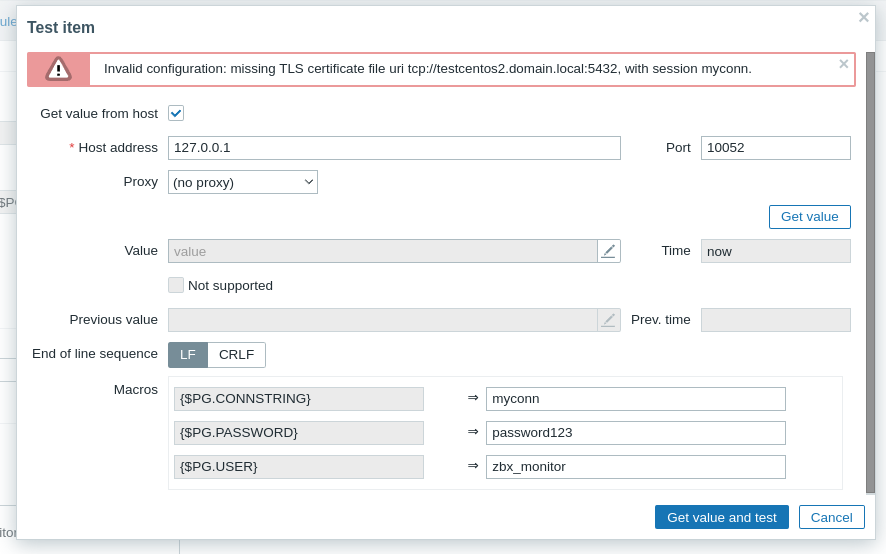
Expected:
Connection should be successful and data should be retreived. Client certificates are in fact optional and used for authentication purposes in case if we want to check the client's identity.
Consult the PostgreSQL documentation about encryption modes and options in libpq and certificates usage:
https://www.postgresql.org/docs/current/libpq-connect.html#LIBPQ-CONNECT-SSLMODE
https://www.postgresql.org/docs/current/libpq-ssl.html#LIBPQ-SSL-PROTECTION