-
Type:
Problem report
-
Resolution: Fixed
-
Priority:
Trivial
-
Affects Version/s: None
-
Component/s: Frontend (F)
-
S25-W42/43, S25-W44/45, S25-W50/51/52/01
-
0.5
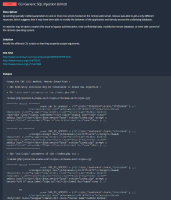
Steps to reproduce:
- Scan using Tenable (Web vulnerability)
Expected:
The parameter autologin must be validate
To fix the issue change the line 51 at :
https://git.zabbix.com/projects/ZBX/repos/zabbix/browse/ui/index.php
must be replaced
from:
$autologin = hasRequest('enter') ? getRequest('autologin', 0) : getRequest('autologin', 1);
to:
$autologin = hasRequest('enter') ? getRequest('autologin', 0) == "1" : getRequest('autologin', 1) == "1";
This way, it prevent the false positive report on Tenable report.