-
Type:
Documentation task
-
Resolution: Fixed
-
Priority:
Minor
-
None
-
Affects Version/s: 7.0.15, 7.2.10
-
Component/s: Frontend (F), Server (S)
-
None
-
Environment:Oracle 9 VM x86_64;
zabbix server, frontend, agent v7.2.10
mysql v8.4.5
nginx v1.20.1
LDAP - osixia/docker-openldap:1.5.0 docker image.
-
Documentation backlog
-
1
Steps to reproduce:
1. Run docker-compose.ym to create Openldap server. Pay attention to mounted volumes. Into /container/service/slapd/assets/config/bootstrap/ldif/custom should be file o_structure.ldif file.
2. Authentication-> LDAP settings:
Enable LDAP authentication, Enable JIT provisioning, Case-sensitive login: Checked
Provisioning period: 1h
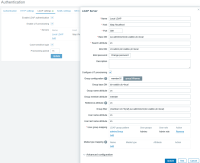
Configure LDAP Server and JIT authentication in zabbix frontend (ZAB_LDAP.png):
Name: Local LDAP
Host: ldap://localhost
Port: 389
Base DN: ou=adminsUnit,dc=zabbix,dc=local
Search attribute: sn
Bind password: admin
JIT Group configuration: groupOfNames
Group base DN: dc=zabbix,dc=local
Group name attribute: cn
Group member attribute: member
Reference attribute: cn
Group filter: (member=cn=%
,ou=adminsUnit,dc=zabbix,dc=local)
User name attribute: cn
User last name attribute: sn
User group mapping:
LDAP group pattern: adminsGroup
User groups: Admins
User role: Admin role
3. Login into zabbix frontend with LDAP user to get provisioned user.
login: admin1sn
password: admin1
4. Delete the user from LDAP server.
Run from openldap container run the command:
ldapmodify -x -H ldap://localhost -D "cn=admin,dc=zabbix,dc=local" -w admin -f /path/to/ delete_admin1-2.ldif
5. Wait an hour. The admin1sn user should automatically moved to group Disabled but it don't happens.
6. Configure LDAP to run anonymous user.
Run from the openldap container the command:
ldapmodify -x -D "cn=admin,cn=config" -w config -H ldap://localhost -f /path/to/allow_anomymous.ldif # check that can get data without autentication ldapsearch -x -H ldap://localhost -b "dc=zabbix,dc=local"
7. Wait an hour. The admin1sn user should automatically moved to group Disabled but it don't happens.
Result:
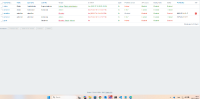
The admin1sn user should automatically moved to group Disabled but it don't happens (see screenshot ZAB_LDAP_result.png).
Expected:
Following the documentation: JIT provisioning also allows to update provisioned user accounts based on changes in LDAP. For example, if a user is moved from one LDAP group to another, the user will also be moved from one group to another in Zabbix; if a user is removed from an LDAP group, the user will also be removed from the group in Zabbix and, if not belonging to any other group, added to the user group for deprovisioned users. Note that provisioned user accounts are updated based on the configured provisioning period or when the user logs into Zabbix. Zabbix doc
Addition: From the same docs: LDAP JIT provisioning is available only when LDAP is configured to use "anonymous" or "special user" for binding. For direct user binding, provisioning will be made only for user login action, because logging in user password is used for such type of binding. Not clear what is "special user". If user from LDAP server/Bind DN field is a "special user" it should work without point 7.
Required more clear definition in documentation.