-
Type:
Problem report
-
Resolution: Unresolved
-
Priority:
Trivial
-
None
-
Affects Version/s: 7.0.19rc1, 7.4.3rc1, 8.0.0alpha1
-
Component/s: Agent2 plugin (G)
Precondition:
- Use docker setup for mtls and/or wrong_san configuration => postgres-zbx.zip

- Extract the files and go to the directory postgres-zbx
- change files owner (docker postgres user, in my case id 999) for certs =>
sudo chown 999:999 ./certs/*
- change files owner for client crt and key (zabbix)=>
sudo chown zabbix:zabbix ./certs/client.crt ./certs/client.key
- change permissions =>
sudo chmod 600 ./certs/*.key sudo chmod 644 ./certs/*.crt
- Use mtls and/or wrong_san configuration for postgresql plugin e.g. =>
Case 1: mtls # Default Plugins.PostgreSQL.Default.Uri=tcp://localhost:5440 Plugins.PostgreSQL.Default.User=root Plugins.PostgreSQL.Default.Database=postgres Plugins.PostgreSQL.Default.Password={use_pasword_from_compose_file} Plugins.PostgreSQL.Default.TLSConnect=verify_full Plugins.PostgreSQL.Default.TLSCAFile={path_to_postgres-zbx_folder}/postgres-zbx/certs/ca-wrong.crt Plugins.PostgreSQL.Default.TLSCertFile={path_to_postgres-zbx_folder}/postgres-zbx/certs/client.crt Plugins.PostgreSQL.Default.TLSKeyFile={path_to_postgres-zbx_folder}/postgres-zbx/certs/client.key # sessions Plugins.PostgreSQL.Sessions.TLS_CA.Uri=tcp://localhost:5440 Plugins.PostgreSQL.Sessions.TLS_CA.TLSConnect=verify_ca Plugins.PostgreSQL.Sessions.TLS_CA.TLSCAFile={path_to_postgres-zbx_folder}/postgres-zbx/certs/ca.crt Plugins.PostgreSQL.Sessions.TLS_CA.TLSCertFile={path_to_postgres-zbx_folder}/postgres-zbx/certs/client.crt Plugins.PostgreSQL.Sessions.TLS_CA.TLSKeyFile={path_to_postgres-zbx_folder}/postgres-zbx/certs/client.key Plugins.PostgreSQL.Sessions.TLS_FULL.Uri=tcp://localhost:5440 Plugins.PostgreSQL.Sessions.TLS_FULL.TLSConnect=verify_full Plugins.PostgreSQL.Sessions.TLS_FULL.TLSCAFile={path_to_postgres-zbx_folder}/postgres-zbx/certs/ca-wrong.crt Plugins.PostgreSQL.Sessions.TLS_FULL.TLSCertFile={path_to_postgres-zbx_folder}/postgres-zbx/certs/client.crt Plugins.PostgreSQL.Sessions.TLS_FULL.TLSKeyFile={path_to_postgres-zbx_folder}/postgres-zbx/certs/client.key ==================================================== Case 2: wrong_san # Default Plugins.PostgreSQL.Default.Uri=tcp://localhost:5438 Plugins.PostgreSQL.Default.User=root Plugins.PostgreSQL.Default.Database=postgres Plugins.PostgreSQL.Default.Password={use_pasword_from_compose_file} Plugins.PostgreSQL.Default.TLSConnect=verify_full Plugins.PostgreSQL.Default.TLSCAFile={path_to_postgres-zbx_folder}/postgres-zbx/certs/ca.crt Plugins.PostgreSQL.Default.TLSCertFile={path_to_postgres-zbx_folder}/postgres-zbx/certs/client.crt Plugins.PostgreSQL.Default.TLSKeyFile={path_to_postgres-zbx_folder}/postgres-zbx/certs/client.key # sessions Plugins.PostgreSQL.Sessions.TLS_CA.Uri=tcp://localhost:5438 Plugins.PostgreSQL.Sessions.TLS_CA.TLSConnect=verify_ca Plugins.PostgreSQL.Sessions.TLS_CA.TLSCAFile={path_to_postgres-zbx_folder}/postgres-zbx/certs/ca.crt Plugins.PostgreSQL.Sessions.TLS_CA.TLSCertFile={path_to_postgres-zbx_folder}/postgres-zbx/certs/client.crt Plugins.PostgreSQL.Sessions.TLS_CA.TLSKeyFile={path_to_postgres-zbx_folder}/postgres-zbx/certs/client.key Plugins.PostgreSQL.Sessions.TLS_FULL.Uri=tcp://localhost:5438 Plugins.PostgreSQL.Sessions.TLS_FULL.TLSConnect=verify_full Plugins.PostgreSQL.Sessions.TLS_FULL.TLSCAFile={path_to_postgres-zbx_folder}/postgres-zbx/certs/ca.crt Plugins.PostgreSQL.Sessions.TLS_FULL.TLSCertFile={path_to_postgres-zbx_folder}/postgres-zbx/certs/client.crt Plugins.PostgreSQL.Sessions.TLS_FULL.TLSKeyFile={path_to_postgres-zbx_folder}/postgres-zbx/certs/client.key
- Import host and items for monitoring latest data => zbx27038.yaml

- Include configuration file for plugin into agent2 =>
Include={path_to_plugin_dir}/postgresql/*.conf
Steps to reproduce:
- Run docker from postgres-zbx directory => docker compose up -d
- (optional) check if containers are running => docker ps
- Run server and agent2
- Check latest data
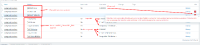
Result: In both cases (mtls and wrong_san) sessions return data for verify_full and verify_ca option.
Examples for mTLS:
Example for wrong san:
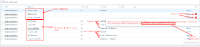
Expected: In both cases only case with verify_ca should return data. TLSConnect=verify_full case should return an error same as for Default configuration.
Note: When you run only one session with verify_full, erros appear as expected.
