-
Defect (Security)
-
Resolution: Duplicate
-
Major
-
None
-
2.2.3
-
Debian 7.3.0
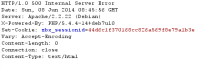
An instance of unserialised non-sanitised user-supplied input was identified in setup.php. The vulnerable code performs unserialisation on the ZBX_CONFIG cookie value as shown below.
// ...
// config
$ZBX_CONFIG = get_cookie('ZBX_CONFIG', null);
$ZBX_CONFIG = isset($ZBX_CONFIG) ? unserialize($ZBX_CONFIG) : array();
$ZBX_CONFIG['check_fields_result'] = check_fields($fields, false);
if (!isset($ZBX_CONFIG['step']))
// ...
Non-authenticated attacker may provide a specially crafted serialised object and achieve an object injection within the application scope.